SolarWinds, the company at the center of Sunburst supply chain attack failed to contain a new zero-day vulnerability being actively exploited in the wild.
Microsoft reported that they had discovered a remote code execution (RCE) vulnerability in SolarWinds’ Serv-U Managed/Secure File Transfer Protocol Server.
The Problem
The discovered zero-day vulnerability ‘CVE-2021-35211’ enables remote threat actors to execute arbitrary code with privileges following successful exploitation. Please find the screenshot of Shodan below:
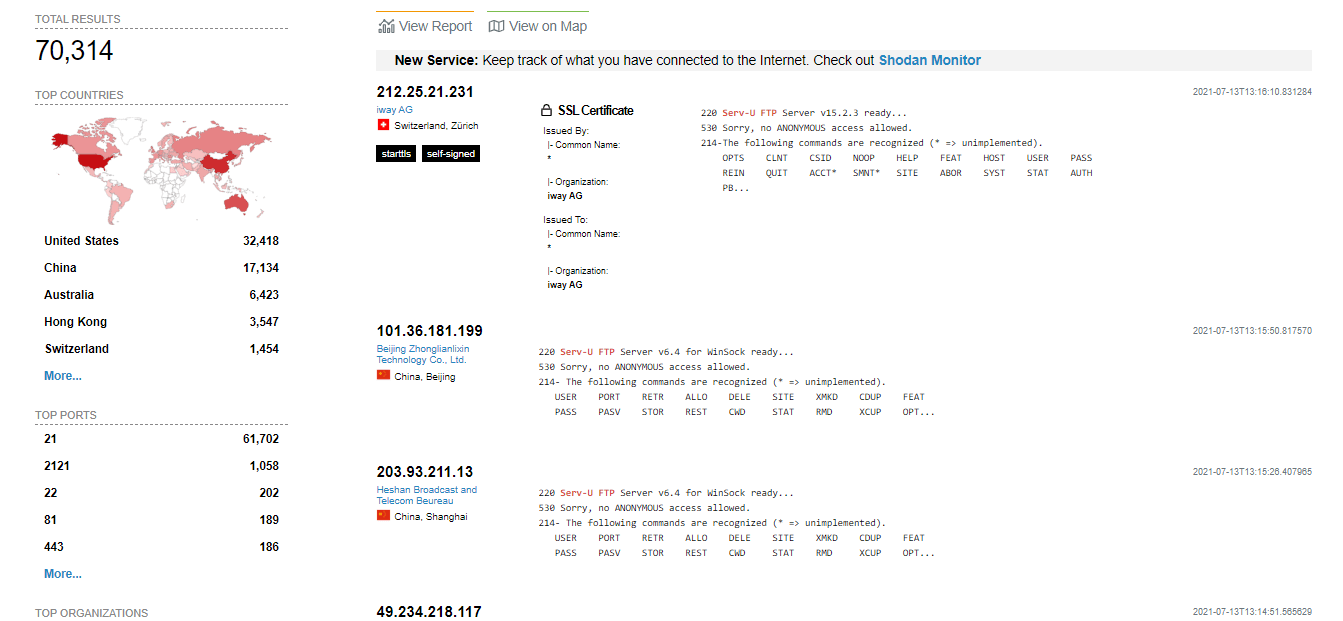
Among 70 K Serv-U FTP servers, 4,000 server allow anonymous login. There are 77,000 Serv-U FTP servers that are been identified by internet scanners, to be vulnerable to this exploit.
The Analysis
This is very similar to Accellion FTA vulnerability, that was used to exfiltrate data from Morgan Stanley, and it became the latest known casualty of hackers exploiting a series of now-patched vulnerabilities.
A threat actor who successfully exploited this vulnerability could run arbitrary code with privileges. An attacker could then install programs; display, change or delete. Based on our study, all Serv-U versions before v15.2.3 HF2, released on Friday, are vulnerable to attacks.
Here are the indicators of compromise that can be used to setup alert conditions on network traffic in your respective SIEM/MDR tool to detect any suspicious activity w.r.t Serv-U exploit:
- 98.176.196.89
- 68.235.178.32
- 208.113.35.58
- Port: TCP 443
- Action String = ‘ConnectionSuccess'
Metmox's Recommendation
- Disabling SSH on affected products prevents exploitation
- Temporarily isolate or block internet access to and from systems hosting the software
- Upgrade to Serv-U 15.2.3 hotfix (HF) 2
- Use a DMZ Secure Gateway, or an enhanced reverse proxy. FTP server (Files and user credentials) stays in the private network, and no inbound ports are required
- Assess the system for evidence of suspicious activity including the IOCs, and obtain a snapshot or forensic disk image of the system for subsequent investigation
- Consider conducting an audit of Serv-U user accounts for any unauthorized changes, and consider resetting user passwords
- Adding additional security controls to prevent the access from unauthenticated sources
- Majority of attacks/data breaches happens via commonly used exploits and existing vulnerabilities. Good patching practices can proactively secure your systems from these attacks
Metmox’s Cybersecurity Practitioners, Professional Services (PS), and Security Specialists are available to help determine the next steps beyond the guidance/guidelines. We provide you with proactive, contextual and effective patch management to ensure that every IT Asset is up to date. We are ranked at #63 by MSSP Alert 2020 among the top 250 Cybersecurity companies of the world.
Our Intelligence-Driven Expert-Led IDEAL Fusion SOC Platform Helps Security Analysts detect and patch vulnerabilities at the speed of bad.
