
You can’t secure what you can’t see! With unique cloud opportunities and benefits, some challenges come with having AWS as your cloud platform.
While the concerns and issues vary widely from company to company and industry to industry, are we prioritizing a Security Strategy ahead of controls and tools?
As the ecosystem and cloud environment gets larger so do the security risks. Misconfiguration, insecure interfaces, and unauthorized access topped the list.

The over whelming digital transformation and consumerization of IT has created an explosion of data and applications in the cloud. But this rapid proliferation of applications, services and moving workloads to the cloud comes with the risk of unmonitored access, security loopholes and data leaks.
Poor visibility into an organization’s cloud usage is a major security challenge prompting many enterprises to reassess and adjust their security posture to suit the dynamic nature of cloud environments. It has been found that an average enterprise invests in 32 different cloud security tools at high cost.
But that is not all, finding qualified cybersecurity expertise is another top challenge for companies battling the shortage of cloud security skills
Each business must be able to answer the following key questions:
- Who has access to which applications and when?
- How can we monitor for key file changes?
- Will we be notified promptly when something anomalous occurs?
- Do we have strong password policies and authentication practices?
- What are the Compliance Controls?
AWS SECURITY RISKS:
A recent global Cloud Security Report released by Check Point and Cybersecurity Insiders shows that the top cloud security threats are unauthorized cloud access (42%), insecure interfaces (42%), misconfiguration of the cloud platform (40%), and account hijacking (39%).
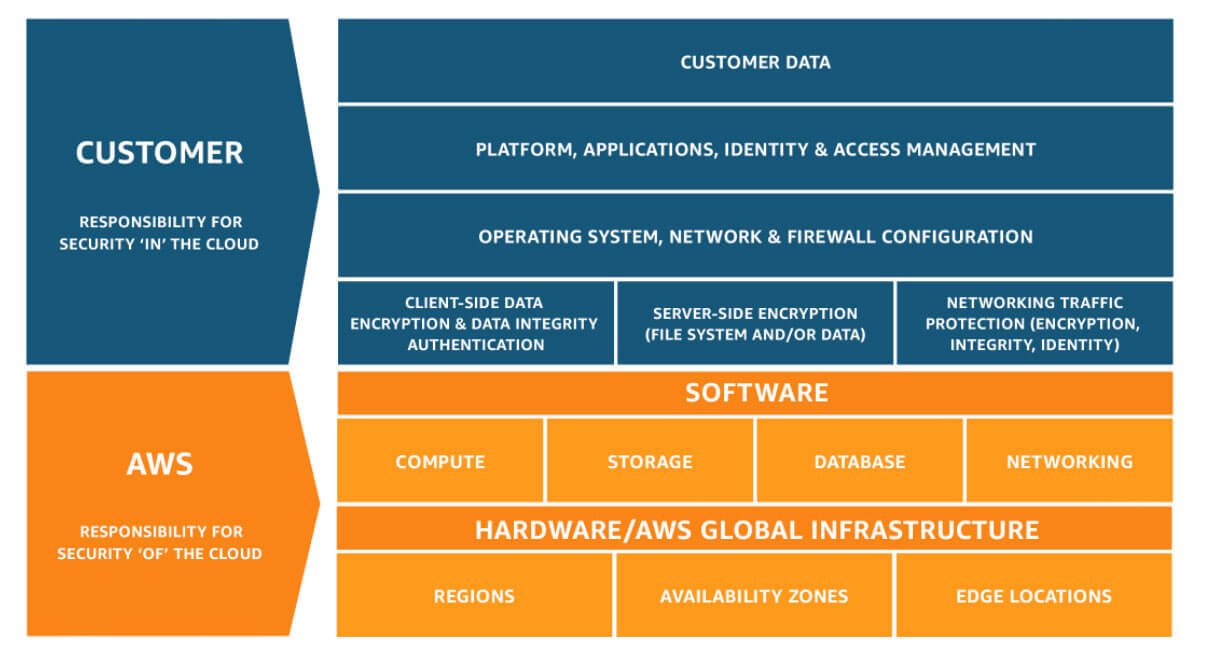
AWS security is not fail-safe and operates on a Shared Security Responsibility model. This means that Amazon secures its infrastructure while you have your own security controls in place for the data and applications you deploy and store in the cloud.
According to RedLock’s research, the average lifespan of a cloud resource is two hours and seven minutes. With multiple cloud accounts and regions, it is highly difficult to detect risks with decentralized visibility. 85% of resources associated with security groups don’t restrict outbound traffic at all.
Administrators often forget to disable root API access. The exposed applications structure requires you to strengthen existing security controls. This includes continuously updating your security configurations with sufficient patching, strong firewall configurations, and proper network security implementations.
AWS S3 buckets are now exposed via additional channels and APIs, which create new security blind spots that hackers are waiting to exploit.
Issues with AWS infrastructure configuration based on the research done by ScienceSoft:
- AWS Firewall Manager.
- Identity and access management (IAM) controls.
- Logging and monitoring tools (Amazon GuardDuty, CloudWatch, and CloudTrail used to implement an efficient SIEM solution as part of a comprehensive AWS monitoring approach).
These AWS infrastructure components may have the following typical misconfigurations:
- Disabled multi-factor authentication for AWS services.
- Amazon CloudTrail is not configured to log the API call history of key AWS services.
- Wide-range permissions for S3 buckets, public cloud storage resources.
- IAM accounts are set up as a single point of access to multiple resources.
- Broad access ranges for AWS Security Groups.
- Startup and configuration scripts containing authorization info.
- Public AWS AMIs (Amazon Machine Image) containing proprietary or sensitive data.
- Machine state snapshots placed in public storage.
Metmox's layered, and in-depth Cloud Security Services offer 24x7 real-time monitoring of applications, devices and servers in the cloud, in short, complete visibility of all security events to minimize vulnerabilities in your cloud infrastructure.
Our Cybersecurity Practitioners, Professional Services (PS), and Security Specialists, and DevOps teams can improve monitoring, compliance, and response with centralized control of all cloud workloads and IaaS, PaaS, container, and virtual environment. Our team conducts penetration testing as part of our security testing services.
Metmox's Recommendations and best practices for AWS security:
- Think of security at every layer. Make sure that every activity is traceable and that you manage privileges meticulously
- Be sure to encrypt every piece of sensitive data that you store in or transmit over your AWS environment.
- Unified, comprehensive security across public, hybrid, and multi-cloud environments give you control over cloud configurations, application and API security management, and access controls, as well as monitoring data in transit, in use, and at rest.
- Establish the proper identity and access management by setting up appropriate permissions.
- Effectively locate security vulnerabilities using cloud security assessments
- Monitor and Audit Server access logs and Cloud watch metrics
- Harden AWS setup using CIS and DISA-STIG benchmarks
As a part of our Managed Cloud Security services, we leverage AWS native tools like Security Hub, Trusted advisor, Route53, WAF, Kinesis, GuardDuty, CloudTrail, CloudWatch, Macie, MFA, Inspector, DDOS mitigation, IAM, Data Encryption and Infra security to provide holistic AWS cloud security.
Our cloud security experts are constantly available to discuss your company’s needs and goals for seamless security.
