What is Third-Party Risk Management?
Third-Party Risk Management (TPRM) is the process of identifying, analyzing, and reducing the risks associated with the third-party vendors/suppliers
Every organization engages third-party to deliver products and services. These vendors can range from few to hundreds to thousands depending on the size of the organization and nature of products and services they offer. Their services and products are needed for day-to-day operations that helps these organizations to deliver back to their clients to manage their markets.
Every vendor carries a potential risk profile while delivering such products and services. Management in most organizations would assume a higher level of security that comes with it. However, no vendor can escape from being a victim of Cyber Attacks, Data Exploits, and other Breaches, Unless the vendor truly understands the security within.
Most organizations are struggling with their TPRM/VRM/SRM Program, as they do not fulfil the activities critical to operations in the areas of vendor risk profiles, compliance, and quality benchmarking (Assessments). The products/solutions as provided by Vendor/Supplier/Third party has some form of weakness which remains underestimated.
How can We Help You?
Metmox can help corporates and SMB to overcome risks that’s not addressed completely, even if you’re managing risks internally. Metmox solutions would help you to gain more insight and have a centralized visibility into risks that concerns more. Metmox Accelerates a Unified Third-Party Risk Program which integrates with GRC functions and IT Assurance services.
Metmox’s Supplier/Third-party risk management program has been designed to an organization of all fit (size and ecosystem). We help our clients to build an efficient and effective Third-party relationship so that your leadership can trust and benefit from the exchange of services/products without any business interruptions, without any risks and minimizing the scope of any potential breach.
Third-Party Risk Services
- We are the interface between our clients and their Vendors
- We assess and evaluate our client’s security objectives, compliance & Internal controls, and Risk appetite (the assessment is mapped back to the vendor assessment to understand if the vendor meets the client’s security requirements)
- We identify the scope and requirement of the product/service and initiate the vendor security assessment process (Pre and Post assessment process; based on the vendor profile)
- We complete the due diligence process (Risk Information: SOC II report, Pen Test Reports, Security Questionnaire, Disclosures, etc.) and provide a detailed analysis and recommendations
- All Risks as identified will be monitored and tracked for risk remediation measures with process enhancements as needed
- We provide vendor risk profile summary at a high level to better engage vendors based on Business/strategy changes
- We integrate and unify various Industry standard and regulatory frameworks to keep our client’s business compliant and safe from cyber incidents (attacks, exploits, breaches, etc.)
Benefits of Third-Party Risk Management
- Management has visibility in their vendor’s risk profile which results in better informed decisions that relate to new and emerging technologies
- Manage time and save cost on resources and infrastructure
- Avoid/Minimize Operation, Legal threats, Regulation actions, Reputation/Brand issues, Data and Security compromises, financial losses, etc.
- Always stay compliant with various regulations and standards
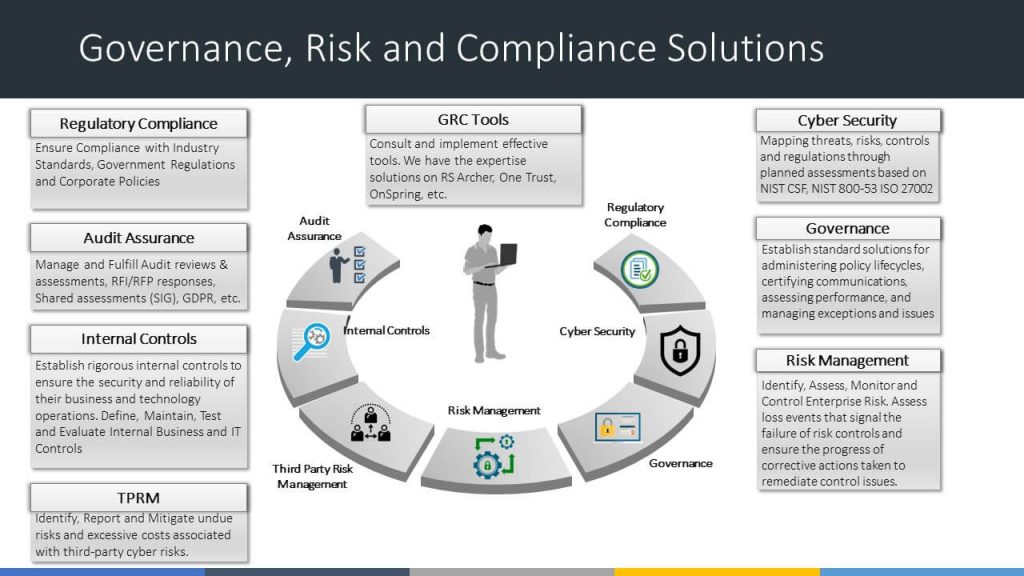
Our array of Services
Importance of TPRM as a Service
Most Organizations, Markets and Governments always face the heat of growing Cybersecurity Malicious activities and incidents. We all know the worst cyber-attacks of 2021 that were experienced by SolarWind, Microsoft Exchange, REvil, Colonial Pipeline, Kaseya, Microsoft's (Print)Nightmare and Log4.
We don’t know who would be next, but we can help you to avoid such unforeseen and unfortunate situations.
Third-Party risks should be a point of great concern. Most organizations do not have the capacity to fulfil the Due-Diligence process on their Vendors. One risk will breach the foundation of the organization that attracts loss of Brand reputation, penalties and more. Third-Party risks can be accounted based on the evaluation areas of Regulatory Compliance, Operational, Legal, Strategic, Financial Risks and Cyber Security events.
Governance Risk and Compliance (GRC) Program
Metmox will bring value to your business with the array of GRC and IT Assurance services.
GRC – IT Assurance Services
Metmox’s Unified Governance, Risk and Compliance Services (GRC) program offers a complete range of IT Audit, Risk and Compliance Assurance Solutions that are tailormade for different industry verticals across small, medium, and large organizations/Enterprises.
We provide these solutions based on the organization’s size, culture, business, sector, geographical presence and spread and relevant regulatory requirements as applied.
Metmox Can overcome the challenges an Organizations/Enterprise faces:
- Overcome the need to optimize ROI arising from the IT Assurance program
- Overcome Resource/skill shortage as needed to deliver IT Assurance Program
- Overcome Distributed domain specialist support. (Support Audit reviews and IT Controls for Internal and Vendor/Third Party Risks)
- Overcome Compliance with specific regulation/Legislation/standards with reference to IT Controls
- Overcome Risk and Compliance risks from Emerging Technology and Infrastructure changes
- Overcome IT Assurance program with Acquire/Merged Organizations
GRC – Enterprise Risk Management
Metmox’s Unified Risk Management establishes an effective risk framework across enterprise-wide with standards and methods for risk identification, assessment, management, and reporting while supporting the risk program to meet the critical and unique needs of our clients.
Metmox Accelerates a unified risk program, validating current security posture and risk landscape to understand so that we can build and provide secure and reliable solutions that not only saves cost, but time and effort.
Metmox has also been delivering Cybersecurity and TPRM Advisory services over a decade now. Our team of consultants can quickly Assess and build unified control library while doing Internal risk assessments and Audit assurance services/projects.
GRC – Risk-Audit Assurance Services
Metmox’s has developed interrelated and unified approach which revolves around Risk-Audit, Compliance, Controls and Assurance Services. We bring in solutions that protect and strengthen every business from people process and technology.
Metmox help clients with the design and implementation of IT risk, Vendor Risk and IT Controls to safeguard businesses involving complex and emerging technologies risk landscape. We help you overcome your challenges and risks as underestimated and undefined in the areas of shadow IT processes.
Metmox is prepared and equipped to resolve risks revolving around “Digital Solutions”. Every business prefers automation so that all processes can be aligned without a margin of error. However, if the automation does not meet the logic and the purpose, it would deviate and would result in creating risks that may go un-noticed.
FAQ
Third-Party risk management primary goals is to manage the overall risk associated with conducting business with Client suppliers/vendors by utilizing the following methods:
- Identify, Categorize and Prioritize Third Party/Suppliers/Vendors
- Perform TPRA using Central questionnaire database as available
- Monitor and track identified risks (including periodic re-assessments as needed). This is a part of due diligence process
- Communicate findings to Business owners and Third Party/Supplier/Vendor
- Project Dashboard reporting to the Management
- Reduce Risks to Client and their Customers
- Vendor/Supplier who handle PII or generally Sensitive Data (ex; Intellectual Property (IP), Financial data, HR application/support vendors, etc.).Vendor/Supplier that develop custom software or hardware for Client/Third-party manufacturing companies
- Vendor/Supplier with access to our network/systems
- Vendor/Supplier performing work at third-party/offshore locations
- Cloud service providers
- Contingent Workforce Suppliers (CWS) and consulting companies
- Minimize exposure and losses for both Client and our customers
- Ensure our compliance with various regulations and standards such as PCI, GDPR, ISO2700X, NIST, etc.
- Enable the business to make informed decisions
- Tracking and monitoring third-party/suppliers/Vendors, helps mitigate and manage Information Security – privacy related risks. This is important due to risk factors such as:
- Recent increased threat from hackers, ransomware/malware, and global threat actors
- The proliferation of the use of new, cutting-edge technologies (ex: Cloud)
- New regional laws and regulations based around cybersecurity and data privacy
TPRM framework consists of:
- Due-diligence process by providing vendor questionnaires
- Reviewing security responses and mapping to security controls
- Review controls concerning policy, procedure, and standards
- Assessing vendors based on security ratings and external disclosures
Advancement of emerging technologies to meet future demands and scalability has left organizations with challenges on how to address third party risks who acts a key spoke in their technology delivery. Underrated risks arising from Vendors (Third Party) exposes revenue loss.
- Risks over data security and integrity for vendors/Third party’s having remote access within or beyond geographical boundaries
- Risks over vulnerabilities and threat landscape in vendor’s environment and map any dependencies with their sub-contracting parties
- Non-Compliance against Regulatory Audits and compliance attestation and Certification through inadequate assessments and activities performed
- Process not aligned/mapped with different control frameworks. Lack of skilled resource to manage and monitor the risks on vendors/Third Party’s
- Lack of awareness and training in a multi network vendor activity and not limited to scope of policies, process people and technology